Threat Watch
Threat Watch provides instant insights to assess and enhance your cybersecurity health across critical categories.
Visit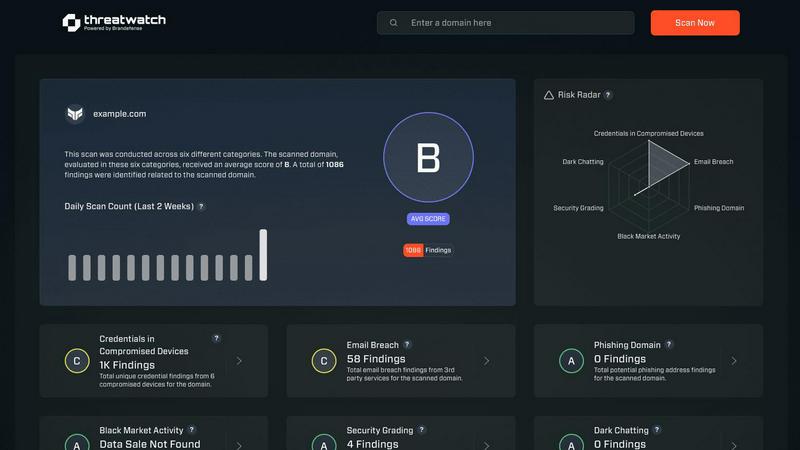
About Threat Watch
Threat Watch is a comprehensive cybersecurity intelligence solution designed to help organizations understand their cyber health. It evaluates critical security categories, including compromised credentials, vulnerable devices, breached accounts, and phishing addresses. By providing real-time insights and automated assessments, Threat Watch empowers companies to identify and prioritize risks effectively. This solution is particularly beneficial for businesses of all sizes seeking to enhance their cybersecurity posture. By uncovering potential vulnerabilities and exposures quickly, organizations can take proactive measures to mitigate risks and safeguard sensitive information. With Threat Watch, users can achieve a clearer picture of their cybersecurity landscape, ensuring they can respond to threats more swiftly and efficiently.
Features of Threat Watch
Real-Time Insights
Threat Watch offers real-time analytics that provide instant visibility into your organization's cybersecurity status. This feature allows users to stay informed about emerging threats and vulnerabilities as they occur, enabling prompt action and better decision-making.
Automated Assessments
This feature automates the evaluation of your organization's security posture, reducing the time and effort required for manual assessments. Automated assessments provide continuous monitoring and quick identification of potential risks, ensuring your defenses are always up to date.
Comprehensive Vulnerability Scanning
Threat Watch conducts thorough scans of your organization's assets, identifying vulnerabilities that may expose you to cyber threats. This comprehensive scanning helps prioritize remediation efforts based on the severity of the vulnerabilities detected.
Dark Web Monitoring
One of the standout features of Threat Watch is its dark web monitoring capability. This feature checks for compromised credentials and breached accounts, alerting users to potential threats that could impact their organization’s security before they can be exploited.
Use Cases of Threat Watch
Small Business Cybersecurity
Small businesses often lack the resources to maintain robust cybersecurity measures. Threat Watch provides these organizations with an affordable way to assess their security posture and identify vulnerabilities, helping them protect sensitive data effectively.
Incident Response Preparation
In the event of a cyber incident, organizations need to respond quickly. Threat Watch equips teams with real-time insights and automated assessments, enabling them to react swiftly to threats and mitigate damage during a security breach.
Compliance and Regulatory Requirements
Many industries have strict compliance and regulatory standards regarding data protection. Threat Watch helps organizations meet these requirements by providing comprehensive vulnerability assessments and detailed reporting on security measures taken.
Employee Training and Awareness
Threat Watch can assist organizations in identifying common phishing threats and compromised accounts. This information can be used to develop targeted training programs for employees, increasing their awareness of cybersecurity risks and promoting safer online behaviors.
Frequently Asked Questions
What types of organizations can benefit from Threat Watch?
Threat Watch is designed for organizations of all sizes, from small businesses to large enterprises. Any organization that seeks to enhance its cybersecurity posture can benefit from the insights and assessments provided by Threat Watch.
How does Threat Watch detect compromised credentials?
Threat Watch utilizes advanced algorithms and monitoring techniques to scan the dark web for compromised credentials. By continuously searching for leaked data, it can alert organizations to potential risks before they become major issues.
Is Threat Watch easy to implement?
Yes, Threat Watch is designed to be user-friendly and easy to implement. Organizations can quickly set up the solution and start receiving valuable insights into their cybersecurity health without extensive technical expertise.
Can Threat Watch integrate with existing security tools?
Threat Watch is designed to complement existing security measures. It can integrate seamlessly with various cybersecurity tools, allowing organizations to enhance their overall security strategy without replacing current systems.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Zignt
Zignt simplifies contract management with automated templates, secure signing, and real-time collaboration for teams.
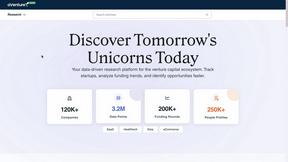
aVenture
aVenture is an AI-driven platform for in-depth research on private companies, investors, and competitive landscapes.